Business
How to beef up workplace cybersecurity in 2019
Cybersecurity threats are becoming more sophisticated each day, and cyber criminals will target companies big or small.

Cyber threats are not only growing with a rapid pace, they are getting more sophisticated, too. Every year, there are incidents of increased cyber attacks on businesses as well as individuals. With the proliferation of e-commerce and people’s growing penchant for online shopping, cyber criminals are ever ready to exploit the conditions as they are able to get hold of important consumer data.
Today, business big or small are under the constant radar of cyber criminals. They are using advanced algorithms and innovative tactics to unleash ransomware, e-fencing, and phishing attacks either to lure employees at workplaces, or to exploit software vulnerabilities. Therefore, the time is ripe to create a potent workplace cyber security culture that can effectively combat the rising cyber attacks.
As an old saying goes, “a chain is as strong as its weakest link.” So don’t let your employees become your weakest link, rather empower them with proper training and resources, so they can effectively guard your organization against malicious hackers. Identity theft is becoming one of the main concerns in the current business landscape, which is leading to serious financial problems. According to the latest identity theft statistics, in the United States 791 million identities were stolen in 2016. This is really alarming!
Here is how you can increase your workplace cybersecurity in 2019 and beyond:
1. Encourage a group effort
To ensure cybersecurity at your workplace, there should be a concerted effort from every quarter. You need to promote safe cybersecurity practices that integrate seamlessly at individual level. It begins with making your employees aware of all the possible cybersecurity threats and amend their ways accordingly in order to mitigate the risks.
Implementation of security essentials is very important to build a secure work environment and employees need to be educated in this regard. They should be trained to understand various types of phishing attacks, better password management, and basics of encryption across the board. If your staff is better prepared that accessing valuable and confidential information could lead to someone else ambushing it, they are far less likely to fall prey to cyber attacks.
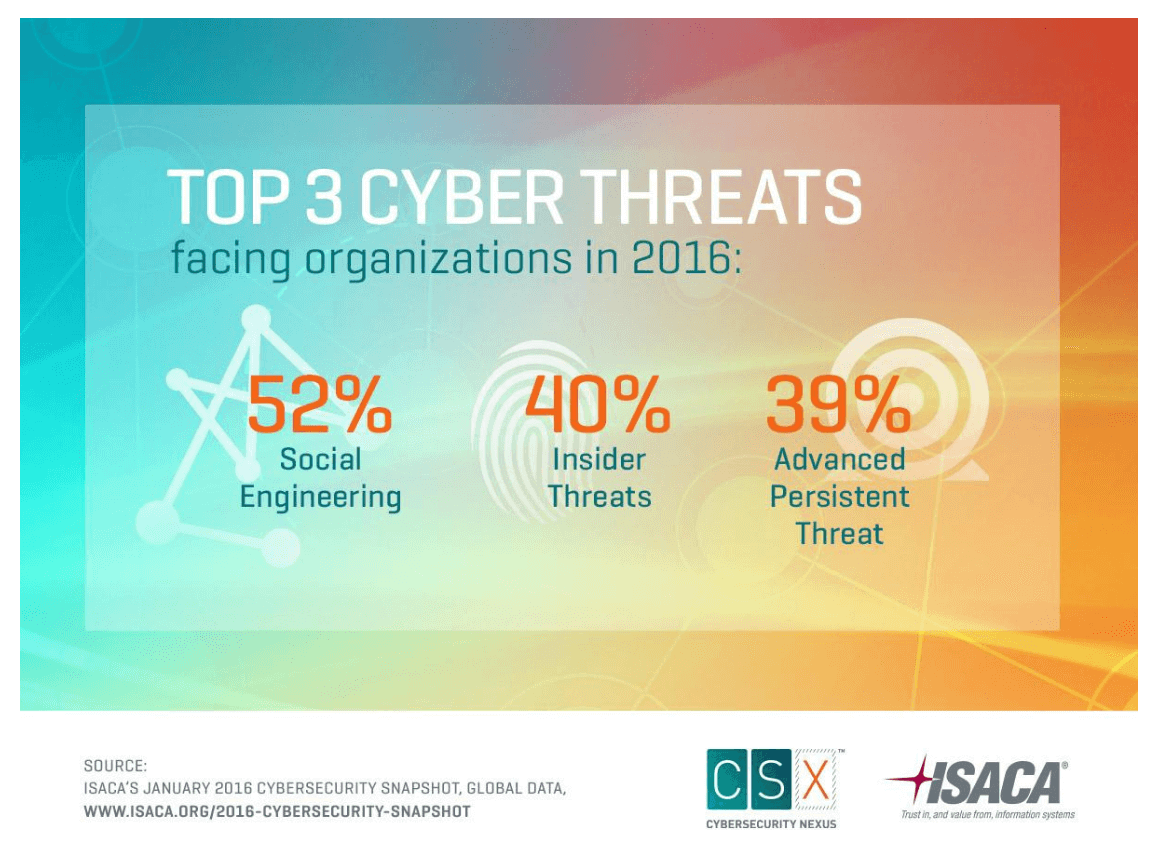
According to an ISACA, CMMI Institute report, a whopping 95 percent of organizations still report a gap between required cybersecurity culture and the current state. As a matter of fact, in many cases cyber attacks are caused by human error and employees are at the core of it. Additionally, hackers are clever enough to use social “engineering techniques” such as creating fake login pages and sending phishing emails.
© Michael Zhou
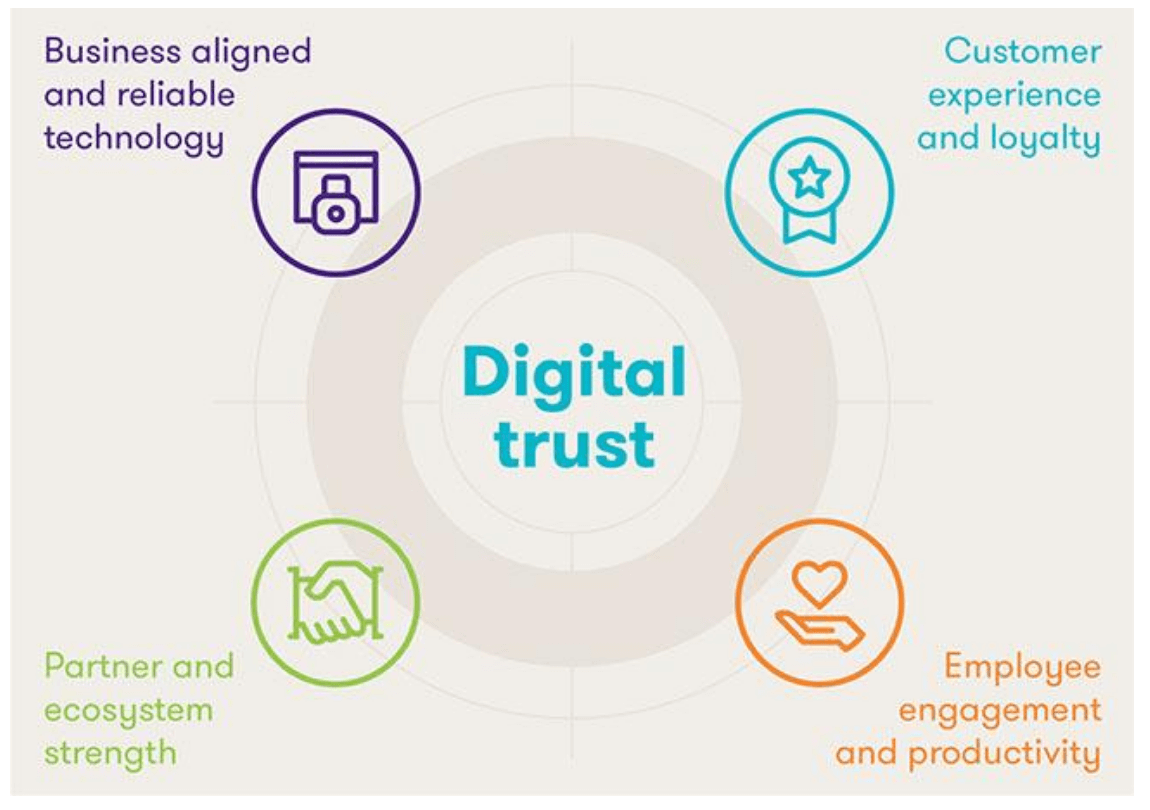
2. Zero trust is now digital trust
As far as workplace cybersecurity is concerned, you should adopt a zero trust security model in your organization. Zero trust doesn’t mean a trust deficit among employees or between employees and higher management, it actually means security will be compromised at no cost.
Today, increasing sophistication of attacks is coupled with insider threats, which should necessitate your IT team to adopt a mindset of ‘we don’t trust anybody.’ This mindset underlines the importance of verifying the identity of anyone or anything moving in or outside your network. It will help you effectively monitor if there is unauthorized access of data taking place. However, you need to ensure employee productivity and customer engagements remain intact. Zero trust should be seen as a digital trust whereby every employee should conform to a comprehensive behavioral profile. As per this profile, employees should furnish information of every device they use and their location.
© Michael Zhou
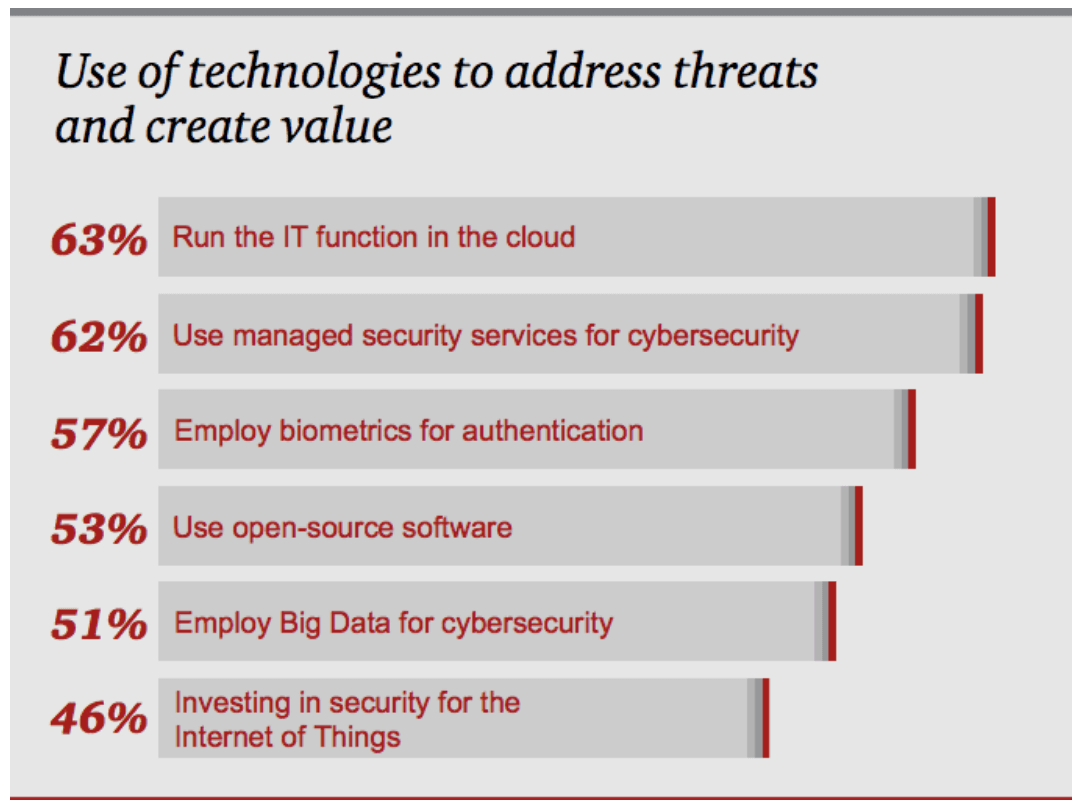
3. Focus on cloud-based security platforms
Organizations have begun to shift their business information to cloud in order to ensure that consumer information and data remain secure. Just like organizations have gravitated towards cloud-based services, cloud-based security has similar appeal—they are platform-delivered, flexible, and scalable. The most important aspect of cloud based security is to ensure that only authorized personnel access the cloud. It will conveniently enable your organization to secure data management, analysis, and access from anywhere.
Cloud-based cybersecurity ensures a secure server management. Traditionally, there were no hard measures to ensure a full server protection as they had a limited built-in mechanism. With cloud web security; traffic gets to the cloud instead of being routed to the servers directly. The traffic also gets filtered before reaching the application system.
© Michael Zhou
There is an increased use of hybrid cloud in today’s technological landscape, which is also associated with some inherent security challenges. In such a scenario, cloud-based security is especially important because of its flexibility and scalability. As a result, you will have additional visibility and monitoring across environments, protecting specific points of networks.
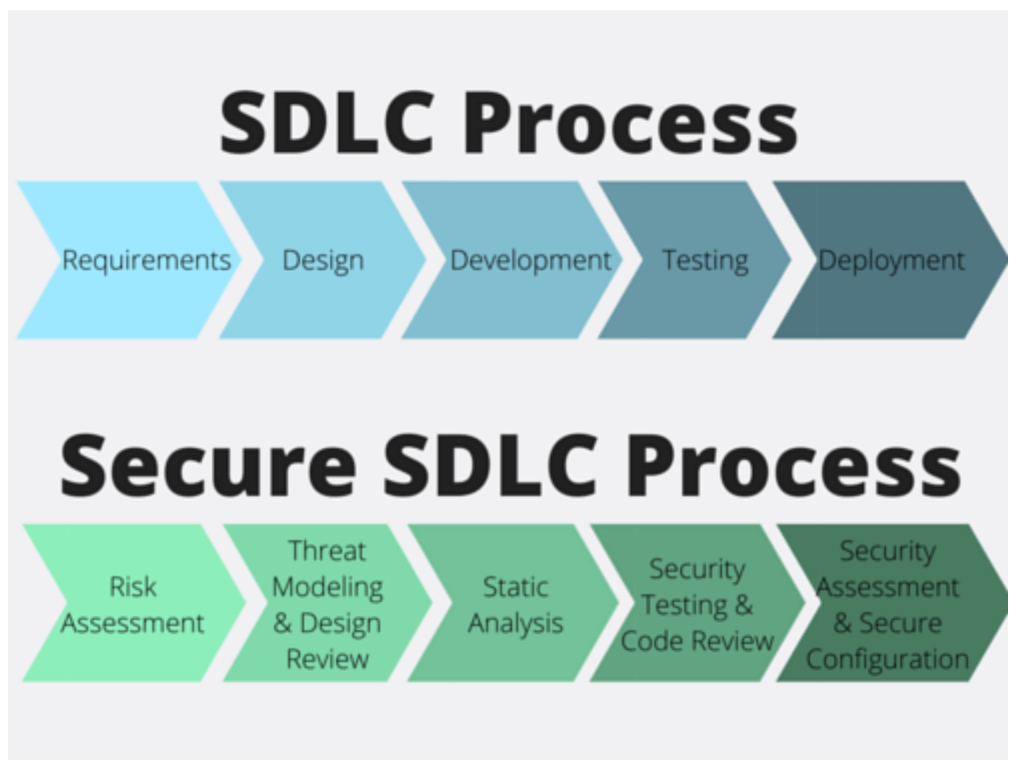
4. Aim to be secure by design
Due to the dynamic nature of technology and related challenges, there is a pressing need for your business to be secure by design. Earlier, organizations would build technology solutions and developed security measures as an afterthought. It led to deployment delays and additional costs. Soon after, the trend shifted towards developing security measures at various stages along the way. Even then, cybersecurity wasn’t given its due preference; it was still at the fag-end.
Now, with the new wave of security challenges and fresh threats popping-up from everywhere, business leaders are recognizing that cybersecurity must be aligned to their overall business goals as well as technology solutions. Thus, as an organization, you must be cyber-prepared at every point in your digital transformation. Cybersecurity must now be factored-in as new applications are conceptualized, designed, adopted, and developed.
An effective approach to secure your organization by design is to incorporate secure development life cycle (SDL). An SDL is the process and activities that your organization agrees to perform for each software or system release. It includes practices such as dynamic assessment of security requirements, threat modeling, and security testing activities.
© Michael Zhou
5. Incorporate intelligence-driven cybersecurity measures
Although Artificial Intelligence is still in its nascent stage, but nonetheless it has already entered fields like healthcare, education, gaming, e-commerce, etc. AI has a huge potential in the field of cybersecurity. Not only businesses but governments are also trying to harness AI and Machine Learning for the protection of their crucial data. It is expected that the year after 2019, organizations will have a sound cybersecurity defense with true AI capabilities.
As cyber attacks have become fast and automated, AI seems to hold the key to be able to respond swiftly or even predictively, rather than reactively, to individual threats. Moreover, in response to the changing landscape of threat perception, AI is more capable of allowing your company’s overall cybersecurity stance to change dynamically.
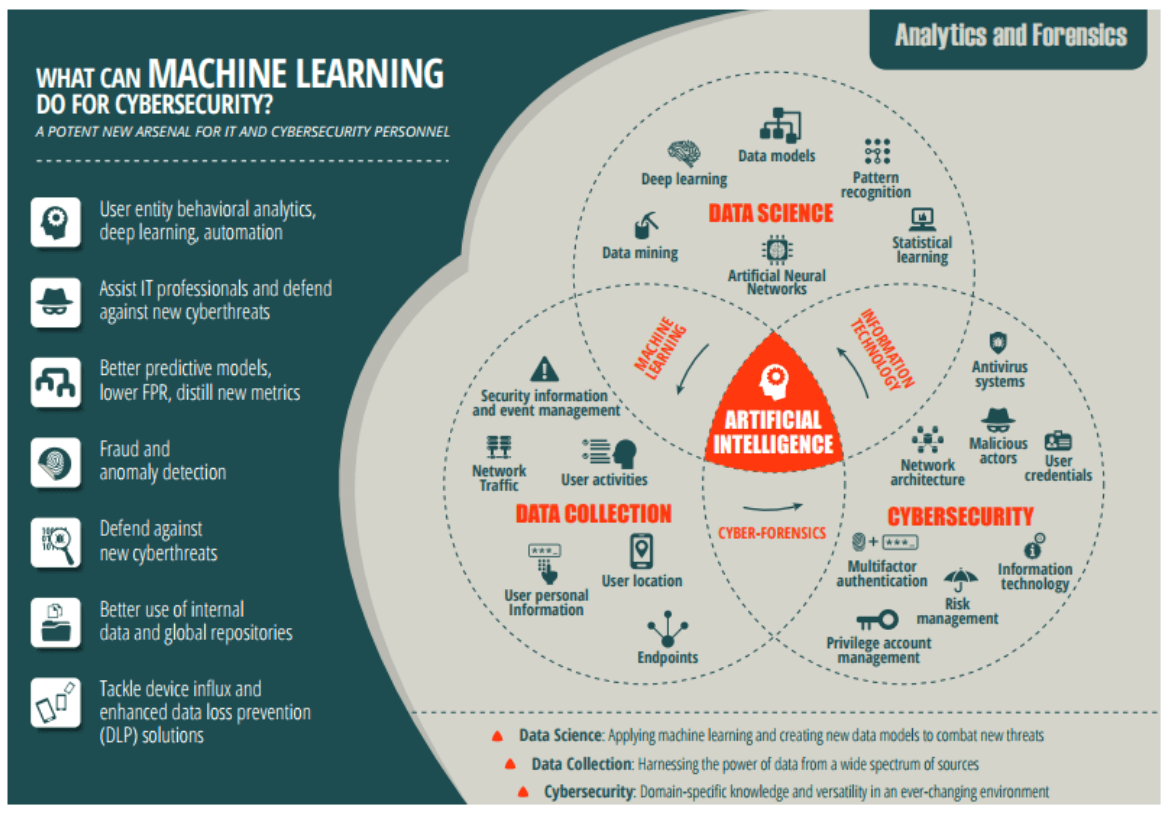
© Michael Zhou
Along with AI, Machine Learning can beef-up your cyber defense by actively gathering intelligence. Thus, machines will start making more of their own decisions and execute changes themselves to minimize risks. For example, once a malware has infiltrated your network, your defense system’s decision-making will roll-out instantaneously.
Conclusion
Cybersecurity is of paramount importance for businesses today. Cyber criminals are exploiting every opportunity to hurl malicious attack on organizations. In all of this, human factor is one of the main vulnerabilities that needs to be addressed effectively and efficiently. Thus, employees have to play a big role in a company’s security perimeter. For that, a safe and secure workplace is the necessary first step towards an impressive cyber defense.
(Featured image by BalticServers.com via Wikimedia Commons. CC BY-SA 3.0.)
—
DISCLAIMER: This article expresses my own ideas and opinions. Any information I have shared are from sources that I believe to be reliable and accurate. I did not receive any financial compensation for writing this post, nor do I own any shares in any company I’ve mentioned. I encourage any reader to do their own diligent research first before making any investment decisions.

-

 Impact Investing1 week ago
Impact Investing1 week agoCDP Approves €1.5 Billion Package to Boost Industry, Renewables, and International Development
-

 Crypto2 weeks ago
Crypto2 weeks agoUniswap and BlackRock Partner to Launch BUIDL in DeFi
-

 Impact Investing2 days ago
Impact Investing2 days agoThe Sustainability Revolution: Driving a Net-Zero, Nature-Positive Economy
-

 Biotech1 week ago
Biotech1 week agoNew Molecular Clues Explain Aggressive Neuroblastoma and Point to Targeted Treatments

























You must be logged in to post a comment Login